N Investment Securities – Remote work in disjoined network environment
Customer Success story
“RemoteView is accompanying N Investment & Securities’
remote access information protection system. ”
N Investment & Securities is creating synergies in all business areas with its asset management capabilities and know-how to dominate the market.
01 Background
When an IT system failure occurs, the recovery speed is most important. For a divided network environment, it took a considerable amount of time for the system team to visit and restore it, making it difficult to respond to failures quickly. Also, the guiding rules allow remote access within the range that meets the security requirements for emergency measures such as failure response and natural disasters. So, N Investment & Securities decided to consider introducing a remote access solution that complies with the security guidelines.
02 Reasons for choosing RemoteView SE
Furthermore, RemoteView SE, deployed at N Investment & Securities, meets all security requirements across various independent network environments as a remote control solution. Additionally, the system at N Investment & Securities is optimized for efficient failure recovery and meets the detailed inspection requirements for access control and information protection certifications. Therefore, this ensures a more stable response to system failures.
1. Securing the pre-approval process with work/records afterward by the manager in charge.
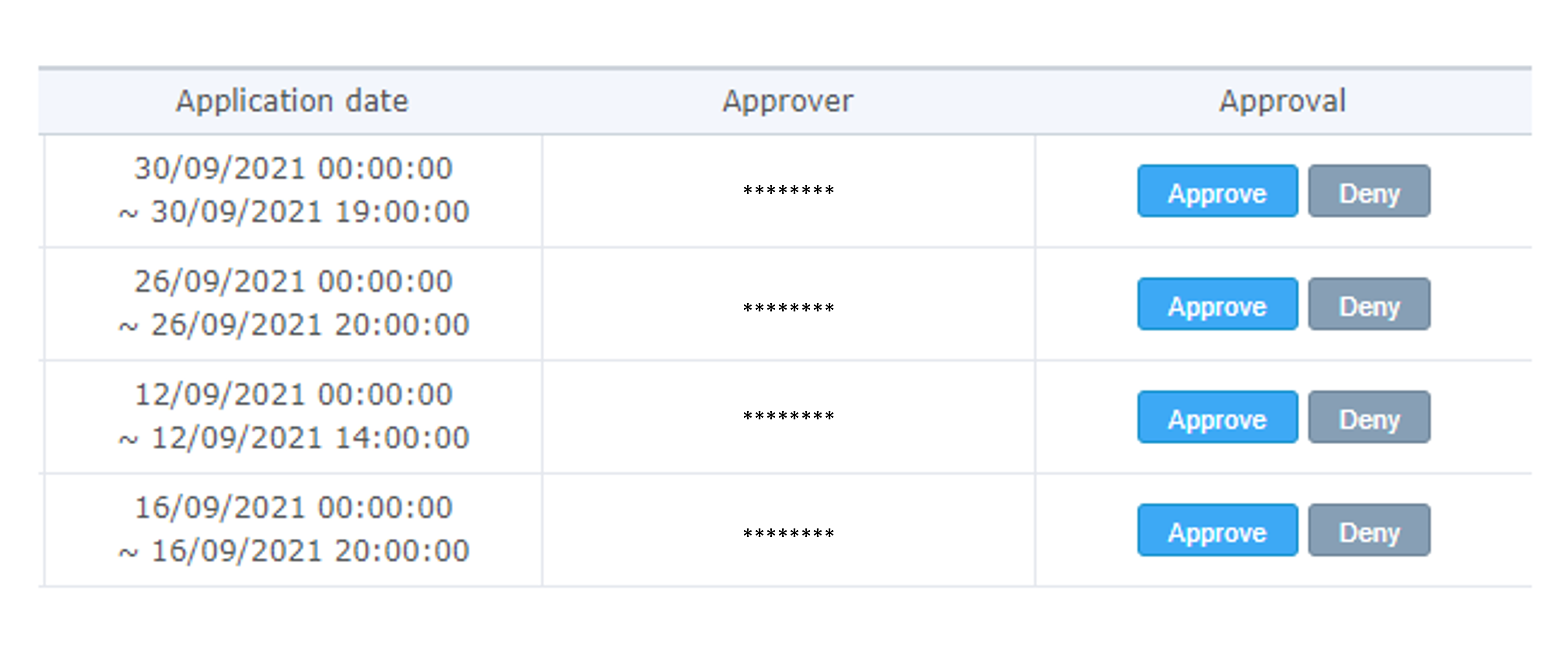
- Specifically designed to permit only manager-approved users, this system also provides remote access logs for thorough post-audit reviews.
2. Improve data security by applying encryption on all communication.
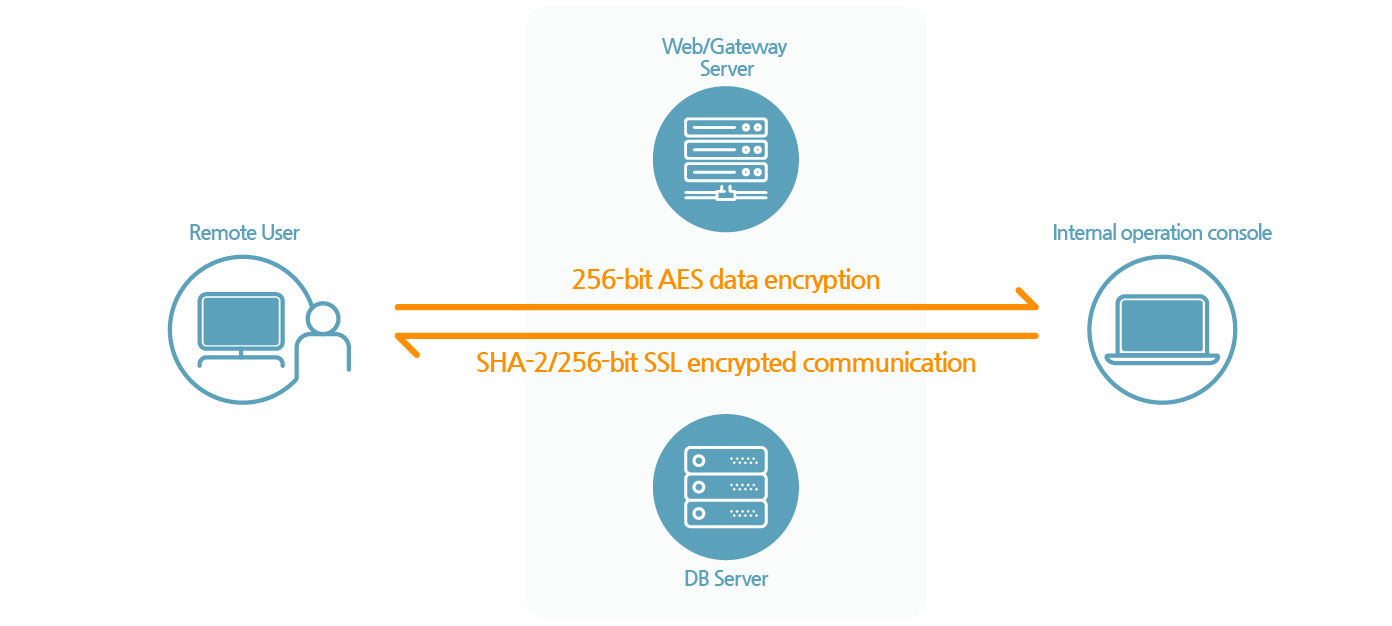
- Before each session, we perform a primary data security process using 256-bit AES encryption for End-to-End protection. In order to initiate a remote session, we activate a secondary security process, securing the channel with 256-bit SSL encrypted communication.
3. Enhanced security by introducing additional authentication methods.
- Then, after initial ID/password authentication, users can enhance security by opting for two-step verification via Google Authenticator, SMS, or email.
4. Real-time logging of records and inspection of all work details to provide audit data

- Moreover, every remote session is recorded in real time, capturing and storing access details such as ID, MAC address, IP address, access date and time, and work history.
Click here
Related article
-

Korea Environment Corporation
Public institutions
-

Korea Authority of Land & Infrastructure Safety
Public institutions
-

Douzone, a enterprise IT solutions provider
IT Solution
-

OA, Multifunction printer solution company, Sindoh
IT Solution
-

Seoul S University
Education
-

Seoul D Women’s University
Education
-

Book sales company – K Book Centre
Sales
-

Household Variety Store – D Shop
Sales
-

Infinite Healthcare, Medical imaging specialists
Healthcare
-

Korea’s most iconic medical facility – S Hospital
Healthcare
-

Digital signage company – Cheonjo
Unmanned equipments
-

Korea’s largest POS solution specialist – Astems
Unmanned equipments
-

Machine/Industrial Machinery Company – H
Manufacturing
-

Leading Display Manufacturer – S Electronics
Manufacturing