How to use Single Sign-On(SSO) in a safe and accurate way?
- Insight
Social Login Service That You Might Have Used At Least Once!
You may have used 'Social Login' when accessing a third-party website or application.
Furthermore, this feature makes signing up and logging in a breeze.
And you can do so effortlessly by linking your preferred social media accounts, like Google, Facebook,
and Twitter, with just a quick agreement to our personal information collection statement.
▲ An example of login using social media
Some say that Social Login is a form of Single Sign-On (SSO), but what exactly is SSO?
What Is Single Sign-On(SSO)?
SSO stands for Single Sign-On, an authentication scheme that allows a user to
access various services using a single ID.
In the past, signing in to multiple websites or applications required the boring process of entering
individual IDs and passwords for each service.
However, SSO allows users to log in with a set of authorization to multiple accounts without
the need to repeat the login process once the user authentication is completed on a platform.
The three components in SSO refers to the user, the Identity Provider (IdP), and the Service Provider (SP)
which works based upon a trust relationship.
The workflow of SSO is as follows. (*SSO processes in the same way on RemoteView)
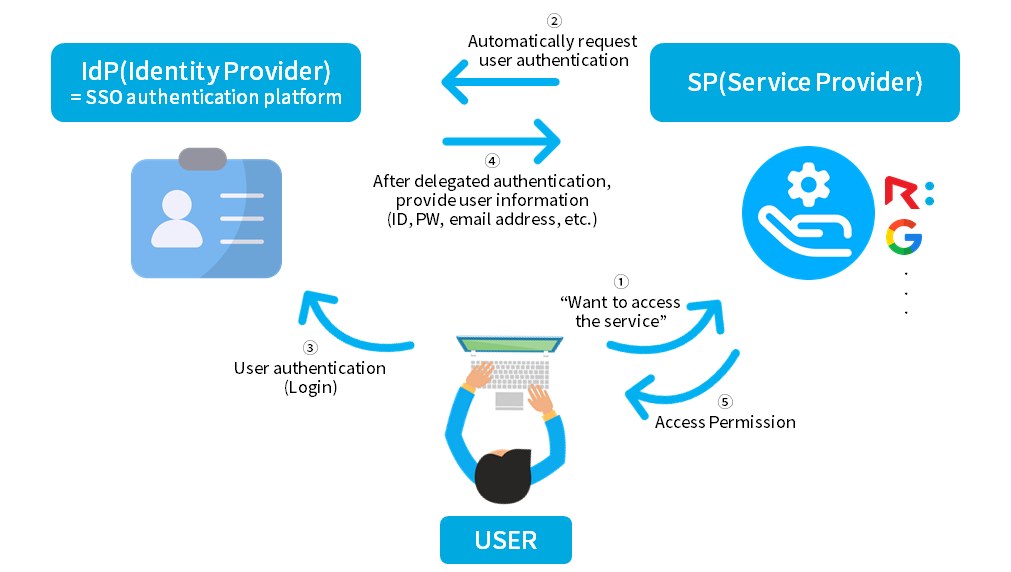
▲ SSO Workflow
*IdP(Identity Provider): An authentication intermediary service that verifies user information and provides access authorization
when a user requests to access SP. e.g. IDaaS (Identity as a Service) solutions.
*SP(Service Provider): Offers web or app services to users. For example, RemoteView, Google Workspace, and more.
Steps:
● 1: User initiates access to a service at the SP (Service Provider) end, such as RemoteView.
● 2: System automatically redirects the user to the IdP (Identity Provider), which acts as the SSO authentication agent.
● 3: IdP authenticates (logs in) the user (Delegated authentication).
● 4: IdP then redirects the user back to the SP, transmitting the user’s information (ID, password, email address, etc.)
used in the authentication process to the SP.
● 5: SP finalizes the login process, allowing the user to use the service.
What Are The Benefits Of SSO?
There are three main benefits: greater security, higher productivity, and enhanced user experience.
Let's take a closer look at each benefit.
01
Greater Security

As more people use cloud computing services such as SaaS(Software-as-a-Service) and IaaS(Infrastructure-as-a-Service),
the number of login credentials used by an employee for each service continues to grow.
Moreover, it is definitely not easy to remember and manage multiple accounts created in this way.
However, SSO allows users to log in to multiple services with a single set of authentication.
Also, wipe out the security risks associated with repeated or lost passwords.
02
Higher Productivity

Can help improve the productivity of IT managers in the business!
Instead of establishing authentication systems for each service used by employees,
managers can control users who access multiple services, systems, and other important resources
with just one set of credentials(ID and password).
03
Enhanced User Experience

It simplifies the login process, allowing instant access to the services they need.
Users do not need to log in multiple times for websites or applications.
When done correctly, SSO services can greatly improve the user experience and make customers happier.
How To Adopt the SSO System Correctly?

SSO enables convenient access to multiple services with a single set of login credentials while reducing
the risk of lost credentials.
However, it also introduces security vulnerabilities, as users who pass the initial authentication process can
freely access the webpage or web server.
In order to address this issue, the 'Zero Trust’ security model is being used.
Zero Trust is a security model based on the principle of ‘Never trust, always verify first!’ and thoroughly verifies the identity of users.
When SSO is paired with Multi-Factor Authentication(MFA), a representative Zero Trust solution,
security can be improved while maintaining convenience.
In order to implement SSO more securely, additional authentication such as one-time password(OTP) or
facial/biometric recognition should be required
when accessing important resources from an untrusted network even after passing initial authentication.
If Your Business Is Interested In Adopting SSO…
With SSO, businesses can achieve convenience, security, and productivity all at once if implemented correctly!
Try SSO-integrated RemoteView based on the Zero Trust security model, and enjoy remote access in a streamlined and safe environment!
Are you considering introducing RemoteView?
Sign up for a demo and start the 14-day free trial of RemoteView.
Integrated Authorization
MFA
Single Sign-On
SSO
Zero Trust